If you’re not familiar with CompTIA (Computing Technology Industry Association) yet, it’s one of the IT industry’s top trade association. Its members encompass large software and hardware vendors as well as small and medium companies, freelancers, instructors, as well as universities.
CompTIA is primarily known for the trainings and associated certifications it is offering. Incidentally, the first industry IT training I was delivering, back in 1999 or early 2000, was a preparatory class for CompTIA’s A+ certfication. It was a great training for a beginning instructor to deliver, as the contents were quite basic, so I could fully concentrate on the delivery aspects.
Currently, the most widely sought-after certifications CompTIA is offering are in the field of information security. CompTIA’s Security+ certification (exam code SY0-601 in the current version as of January 2021), is considered to be an ideal certification for beginners, before moving on to more challenging certifications. An overview of the certification can be found at CompTIA’s official website, practice questions and exam objectives can be requested here.
As part of our university’s membership in CompTIA’s academic program, I reviewed the official training materials to evaluate their suitability as part of a practice-oriented lab course in our Bachelor of Science program for Information Security and Data Privacy at Ansbach University of Applied Sciences.
The course materials are provided in ebook form with approximately 700 pages of densely-packed contents, intended to be delivered as a five-day industry training. The class also comprises 32 lab exercises that complement the theoretical aspects nicely.
Here’s the overview of the chapters as they are recommended to be delivered over five days („Close“ indicates the end of a training day in the schedule).
| 01A | Compare and Contrast Information Security Roles |
| 01B | Compare and Contrast Security Control and Framework Types |
| 02A | Explain Threat Actor Types and Attack Vectors |
| 02B | Explain Threat Intelligence Sources |
| 03A | Assess Organizational Security with Network Reconnaissance Tools |
| 03B | Explain Security Concerns with General Vulnerability Types |
| 03C | Summarize Vulnerability Scanning Techniques |
| 03D | Explain Penetration Testing Concepts |
| 04A | Compare and Contrast Social Engineering Techniques |
| 04B | Analyze Indicators of Malware-based Attacks |
| Close | |
| 05A | Compare and Contrast Cryptographic Ciphers |
| 05B | Summarize Cryptographic Modes of Operation |
| 05C | Summarize Cryptographic Use Cases and Weaknesses |
| 05D | Summarize Other Cryptographic Technologies |
| 06A | Implement Certificates and Certificate Authorities |
| 06B | Implement PKI Management |
| 07A | Summarize Authentication Design Concepts |
| 07B | Implement Knowledge-based Authentication |
| 07C | Implement Authentication Technologies |
| 07D | Summarize Biometrics Authentication Concepts |
| 08A | Implement Identity and Account Types |
| 08B | Implement Account Policies |
| 08C | Implement Authorization Solutions |
| 08D | Explain the Importance of Personnel Policies |
| Close | |
| 09A | Implement Secure Network Designs |
| 09B | Implement Secure Switching and Routing |
| 09C | Implement Secure Wireless Infrastructure |
| 09D | Implement Load Balancers |
| 10A | Implement Firewalls and Proxy Servers |
| 10B | Implement Network Security Monitoring |
| 10C | Summarize the Use of SIEM |
| 11A | Implement Secure Network Operations Protocols |
| 11B | Implement Secure Application Protocols |
| 11C | Implement Secure Remote Access Protocols |
| 12A | Implement Secure Firmware |
| 12B | Implement Endpoint Security |
| 12C | Explain Embedded System Security Implications |
| Close | |
| 13A | Implement Mobile Device Management |
| 13B | Implement Secure Mobile Device Connections |
| 14A | Analyze Indicators of Application Attacks |
| 14B | Analyze Indicators of Web Application Attacks |
| 14C | Summarize Secure Coding Practices |
| 14D | Implement Secure Script Environments |
| 14E | Summarize Deployment and Automation Concepts |
| 15A | Summarize Secure Cloud and Virtualization Services |
| 15B | Apply Cloud Security Solutions |
| 15C | Summarize Infrastructure as Code Concepts |
| 16A | Explain Privacy and Data Sensitivity Concepts |
| 16B | Explain Privacy and Data Protection Controls |
| Close | |
| 17A | Summarize Incident Response Procedures |
| 17B | Utilize Appropriate Data Sources for Incident Response |
| 17C | Apply Mitigation Controls |
| 18A | Explain Key Aspects of Digital Forensics Documentation |
| 18B | Explain Key Aspects of Digital Forensics Evidence Acquisition |
| 19A | Explain Risk Management Processes and Concepts |
| 19B | Explain Business Impact Analysis Concepts |
| 20A | Implement Redundancy Strategies |
| 20B | Implement Backup Strategies |
| 20C | Implement Cybersecurity Resiliency Strategies |
| 21A | Explain the Importance of Physical Site Controls |
| 21B | Explain the Importance of Physical Host Security Controls |
The quality of the training materials: definitely great
Looking at the contents of the instructor/student materials, it is apparent that CompTIA’s authors have invested quite some time and effort into developing these. The course is well-rounded in itself and does a great job of covering all the basics of information security. For students that need more introductory materials in fundamental areas like Linux or networking, CompTIA is offering separate courses and certifications like A+, Linux+, or Network+.
The training materials are well written and follow a clear didactical outline and comprise more than the fundamental aspects of information security. Anyone thoroughly studying the course and preparing for the associated certification is well set up to continue their learning journey with more challenging aspects of IT security. CompTIA also offers advanced cybersecurity courses and certifcations like the CySA+, PenTest+, or CASP+.

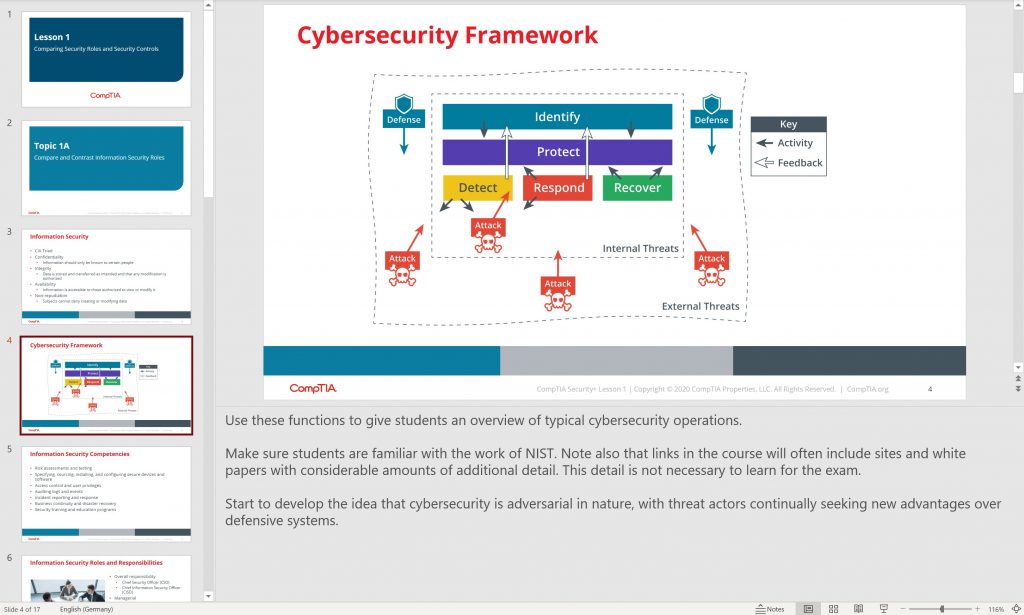
A sample from the official course materials 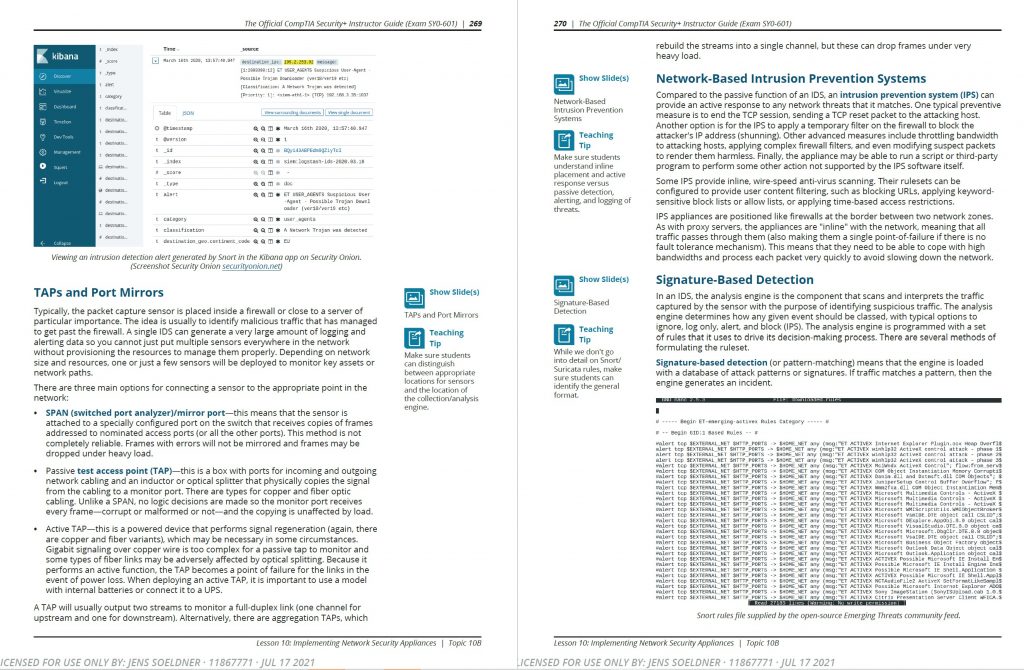
A sample from the official course materialsC
CompTIA’s Security+: a great introductory course for infosec beginners
In short, CompTIA did a great job with its Security+ training. It’s a comprehensive and well-planned course, suitable both for adoption in a commercial as well as applied academic context. If you’re considering adopting it, reach out to one of many training partners. If you intend to become a commercial or academic training partner, Christina Allmeroth from CompTIA Germany is more than happy to advise.

Recent Comments