Short Description:
By defining Firewall:Bypass (or changing this field from internal to public address or vice versa) on NAT-rule someone having only networking privileges can circumvent any security rules defined in the gateway firewall.
Let’s assume as a Security Admin we want to block ICMP for an example, so we create the below displayed block icmp rule as security rule
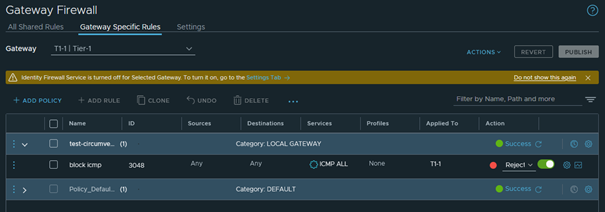
Here is an example traceroute after setting this GWY Firewall Rule
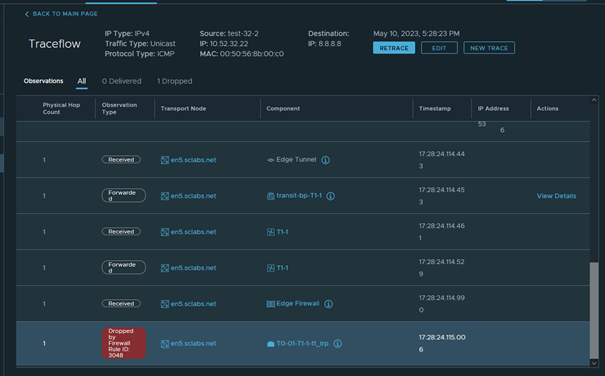
So our rule is successfully blocking any outgoing (but also incoming) ICMP
Now if a Network administrator without any security privileges does not want to have that restriction what can he do on NSX ?
Quite simple he can define a NO-NAT rule and specify to BYPASS any Gateway Firewall rule on that Gateway
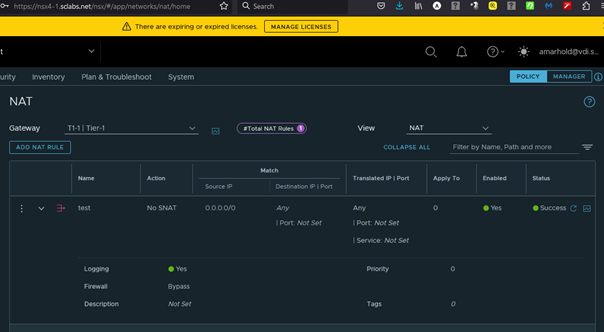
NOTE: that here I am using NO-SNAT and a general wildcard for the source address as an extreme example but it equally works with any SNAT or DNAT and more specific addresses
And the result is a complete bypass of the previous defined rule and we can successfully Ping any outside address
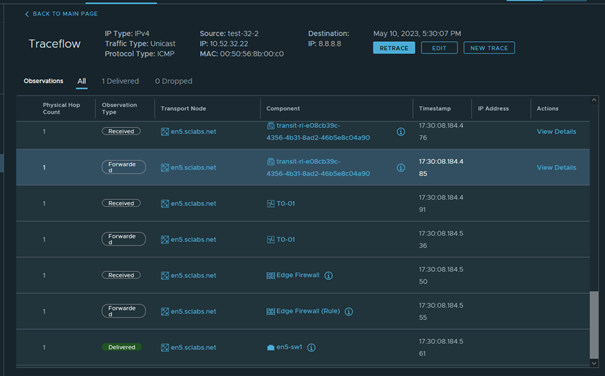
Resume
- The Security relevant design flaw lies in the fact, that the firewall setting in the NAT rule is highly security relevant, but can be set using only networking privileges.
- And NSX-GUI is used by Networking and Security Admins quite separately
- IMHO it would be more secure to allow setting/changes on the firewall field in the NAT rules only with appropriate security privileges.

Recent Comments